Видео с ютуба Example Of Public Key Cryptography

Public Key Cryptography - Computerphile

Asymmetric Encryption - Simply explained

Public and Private Keys - Signatures & Key Exchanges - Cryptography - Practical TLS

Public Key Encryption (Asymmetric Key Encryption)

Public Key Cryptography: RSA Encryption

Lec-83: Asymmetric key Cryptography with example | Network Security

Encryption and public keys | Internet 101 | Computer Science | Khan Academy

Tech Talk: What is Public Key Infrastructure (PKI)?

FastAPI X Next.JS: 3 - Using SSH key with GitHub

encryption explained | Public key cryptography

What is Public Key Infrastructure (PKI) by Securemetric

How asymmetric (public key) encryption works

Fundamentals of Public-Key Cryptography

Symmetric Key and Public Key Encryption

Public Key Cryptography

Prime Numbers & Public Key Cryptography

The RSA Encryption Algorithm (1 of 2: Computing an Example)
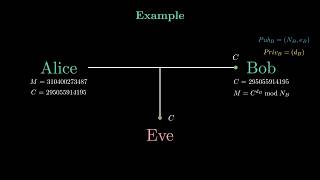
The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.

What Is Public Key Infrastructure (PKI)?

Encryption - Symmetric Encryption vs Asymmetric Encryption - Cryptography - Practical TLS